An intrusion detection system is a device or software application that monitors a network or systems for malicious activity or policy violations.
IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that detects malicious traffic on a network is an example of an NIDS. NIDS let you monitor network traffic, looking for specific activity, and generating alerts.
NIDS can be hardware or software-based systems and, depending on the manufacturer of the system, can attach to various network mediums such as Ethernet, FDDI, and others. This article focuses on software-based NIDS only (we will cover HIDS in a separate article).
NIDS can protect hundreds of computer systems from one network location. This helps make them a cost effective solution and easier to deploy than a HID. NIDs also provide a broader examination of a corporate network via scans and probes, and also protect devices such as firewalls, print servers, VPN concentrators and routers. Additional benefits include flexibility with multiple operating systems and devices, and protection against bandwidth floods and DoS attacks.
Here is our verdict on the finest software-based NIDS. We only include free and open source software. Maltrail is a half-way house between an intrusion detection system and a malware scanner.
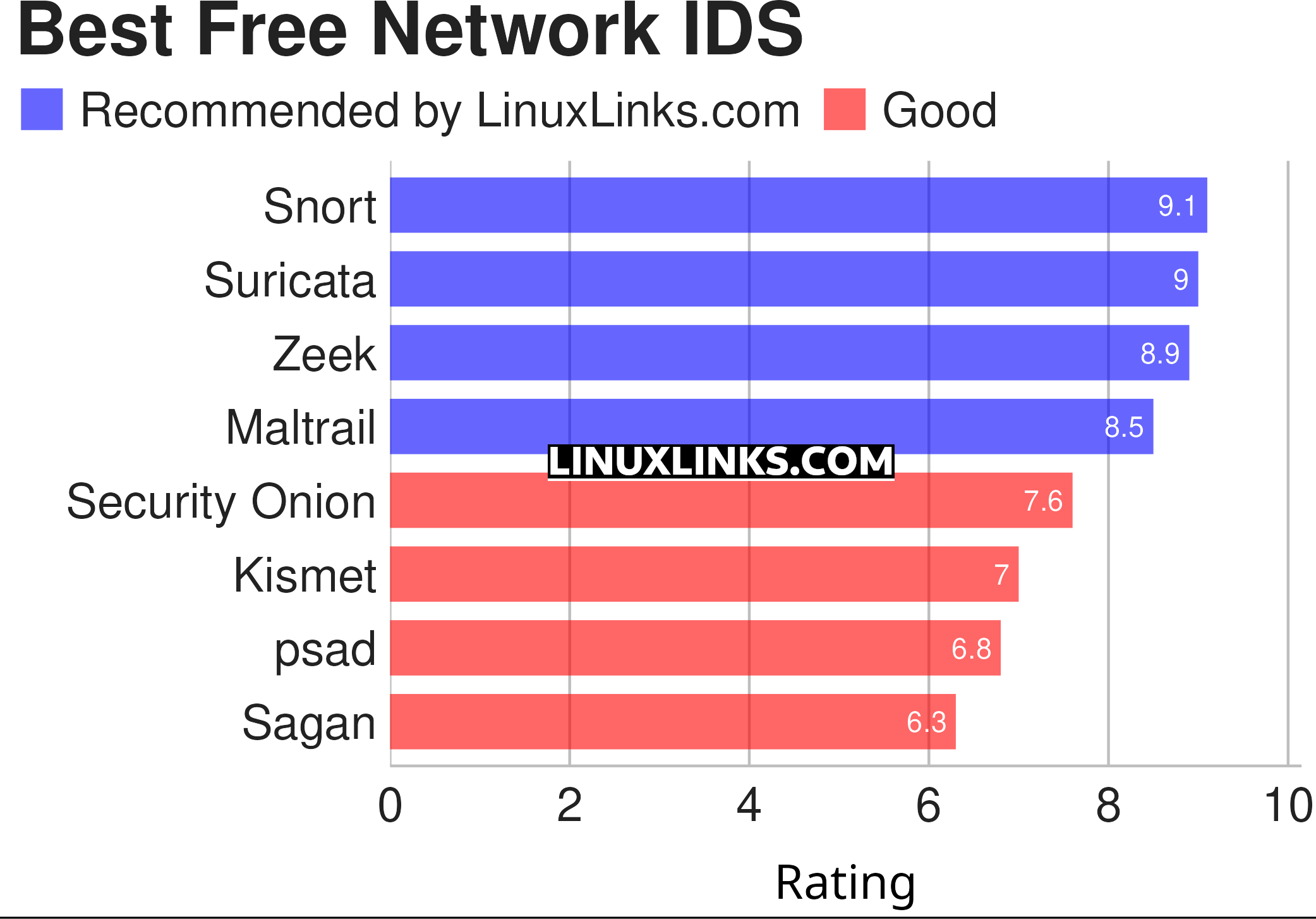
Let’s explore the 8 NIDS. For each application we have compiled its own portal page, a full description with an in-depth analysis of its features, together with links to relevant resources.
| Network Intrusion Detection Systems | |
|---|---|
| Snort | Intrusion detection/prevention with real-time traffic analysis/packet logging |
| Suricata | High performance Network IDS, IPS and Network Security Monitoring engine |
| Zeek | (formerly Bro) Powerful network analysis framework |
| Mailtrail | Lightweight malicious traffic detection system |
| Security Onion | Platform built by defenders for defenders |
| Kismet | Wireless intrusion detection, wireless network and device detector, and more |
| psad | Intrusion detection and log analysis with iptables |
| Sagan | Multi-threads, high performance log analysis engine |
This article has been revamped in line with our recent announcement.
 Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Spotted a useful open source Linux program not covered on our site? Please let us know by completing this form. The software collection forms part of our series of informative articles for Linux enthusiasts. There are hundreds of in-depth reviews, open source alternatives to proprietary software from large corporations like Google, Microsoft, Apple, Adobe, IBM, Cisco, Oracle, and Autodesk. There are also fun things to try, hardware, free programming books and tutorials, and much more. |

Greetings. I find your article interesting, but I am curious about one thing. What is your basis for comparison? In other words, if these are “best”, what is there that makes one better than another, and these better than other offerings?
This type of question is covered in our FAQ