A web application firewall (WAF) is a type of application firewall that lets you see and analyze HTTP traffic to and from a web application. It has the objective of preventing attacks that seek to deny service and steal data. It gives the administrator direct control over the requests and the responses passing through the system without needing to modify backend code. A WAF differs from a standard firewall by protecting a specific web application or set of web applications. And it does this without actually touching web applications.
Unprotected web applications are the easiest entry point for criminals and vulnerable to a number of attack types. Once a web application security vulnerability is discovered, it must be promptly fixed. Virtual patching using a WAF or patching the web application code directly are two solutions. Preventing attacks in application code can be difficult and may need painstaking maintenance, patching and monitoring at multiple layers of the application topology. And web application attacks are the main cause of data breaches. About 75% of all attacks are focused at the web application level. Most websites suffer dozens of attacks every day and some popular sites suffer, on average, a thousand attacks per hour. WAFs are deployed to add an external security layer; this improves a system’s security. They detect and prevent attacks before they reach web applications.
In particular, WAFs protect against the most important web application security risks, such as SQL injection, illegal resource access, buffer overlows, cross-site scripting, file inclusion, HTTP protocol violations, cookie poisoning, and others. Cross-site scripting is probably the most frequent vulnerability affecting web applications of all sizes and complexity.
The software also guards against newly discovered vulnerabilities. Only web application scanners will uncover the application vulnerabilities that criminals are most likely to exploit.
It’s important to configure a WAF to enforce HTTP protocol compliance. Enforcing HTTP protocol compliance, at least during an attack, will thwart evasion techniques, as well as buffer overflow and DoS exploits.
Web application firewalls detect requests from common scanning and hacking tools like Nikto, SAINT, and Nessus based on header agent information. They can also block scanning tools by detecting a frequent number of security violations in a specific time period. WAFs therefore reduce the risk of attackers discovering vulnerabilities in a site.
Securing data, applications and websites from potential and recurring web attacks requires careful planning and investment. It’s important to remember WAFs are only part of a security solution. They should be used together with other security software.
Here’s our verdict captured in a legendary LinuxLinks chart.
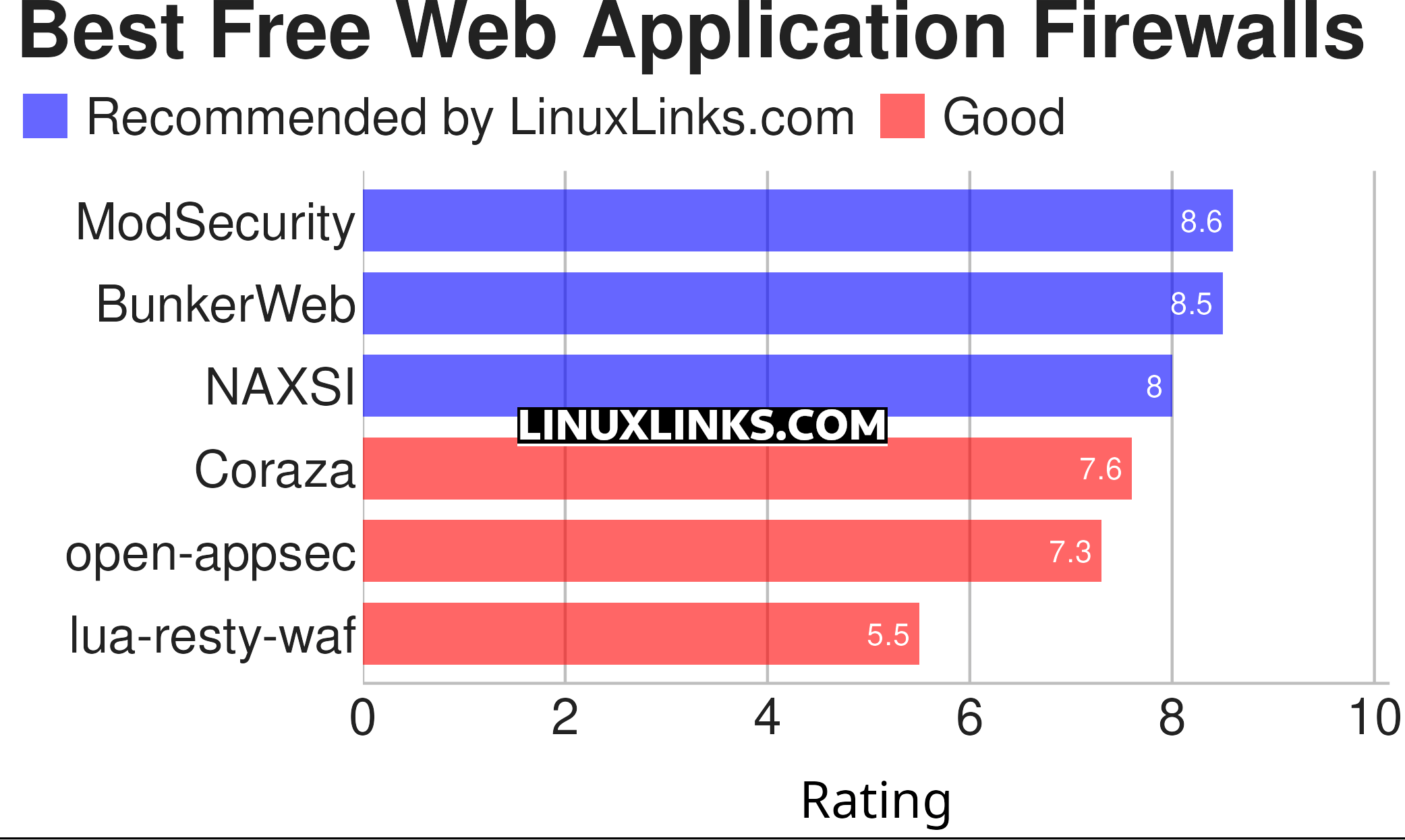
Let’s explore our recommended WAFs. They all run on regular PCs – no proprietary hardware is needed. They are free software – all are published under an open source license. By having full access to the source code, users have the freedom to customize and extend the software. Click the links to learn more about each WAF.
| Web Application Firewalls | |
|---|---|
| ModSecurity | Web Application Firewall Engine for Apache, IIS and Nginx |
| BunkerWeb | Next-generation Web Application Firewall |
| NAXSI | Nginx Anti XSS & SQL Injection |
| Coraza | Enterprise grade, Golang port of ModSecurity |
| open-appsec | Automatic web application and API security using machine learning |
| lua-resty-waf | High Performance WAF Built on the OpenResty Stack |
This article has been revamped in line with our recent announcement.
 Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Spotted a useful open source Linux program not covered on our site? Please let us know by completing this form. The software collection forms part of our series of informative articles for Linux enthusiasts. There are hundreds of in-depth reviews, open source alternatives to proprietary software from large corporations like Google, Microsoft, Apple, Adobe, IBM, Cisco, Oracle, and Autodesk. There are also fun things to try, hardware, free programming books and tutorials, and much more. |

