In Operation
User interface and ease of use
Backup software should be easy to use. A clear and intuitive user interface will particularly be useful for non-technical users.
Setting up your first backup is straightforward with the web-based interface. Click Add backup and choose the option Configure a new backup. There’s also an option to load a configuration from an exported job or a storage provider.
You’ll be asked to choose a name for the backup with an optional description. By default AES-256 encryption is chosen, and you can choose a passphrase. Next you’re asked to choose a storage type and folder path for the backup destination, and the source data to be backed up. You can apply filters and apply exclusions (such as hidden files, system files, temporary files, as well as files larger than a specified size).
The interface is well designed. It’s easy to use and stylish to boot. You should be able to make your first backup without reading any documentation. We did!
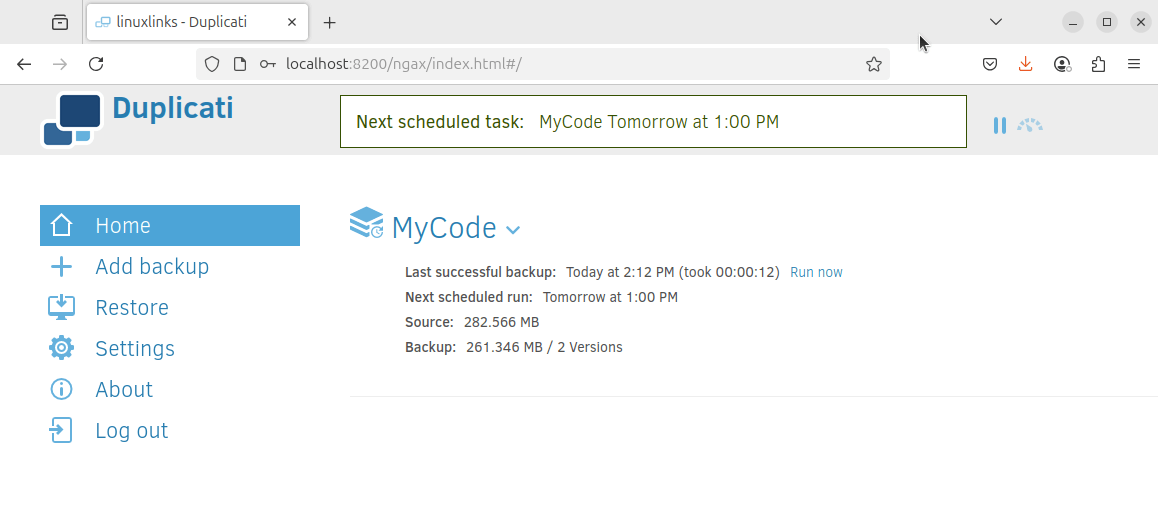
There’s also a command line interface available which lets you run all Duplicati operations without needing a server instance running.
Automation and Scheduling
Performing backups manually is prone to mistakes, omissions, and delays. Good backup software should automate the backup process. Scheduling backups offers a level of consistency that helps keep the backup process reliable.
Duplicati scores quite well. There are scheduling options available including defining which days to run backups, and how often to run them. By default backups are run automatically but this can be disabled. We’d prefer a bit more flexibility such as the ability to add cron expressions.
Storing backups
Efficiency comes from avoiding duplication of file storage. File compression is also an important factor. Encryption ensures security of your files to protect from unauthorized access. Even if backup files are stolen, the actual data cannot be deciphered without a decryption key.
Duplicati performs a full backup initially. Afterwards, Duplicati updates the initial backup by adding the changed data only. That means, if only small parts of a huge file have changed, only those tiny parts are added to the backup. This saves time and space and the backup size usually grows slowly. Data deduplication is enabled automatically by Duplicati. This means that multiple copies of the same file are only stored once.
All backup data is compressed before it is encrypted and uploaded. Duplicati supports Zip/Deflate or 7z/LZMA2 compression.
Encryption is also supported but not mandatory. By default, it uses the state-of-the-art AES-256 encryption, but there’s also GNU Privacy Guard available. All data is encrypted locally before it is transferred to the remote storage system.
Reporting and Testing
Regularly testing your data backup strategy is essential for ensuring that backups are functioning as expected and that any configuration changes don’t cause any unexpected errors. It also allows you to identify and address any backup issues.
We can perform a direct restore from backup files or restore from configuration. Restore a backup to the local machine, a new installation of Ubuntu, or a different computer.
Errors in backups are reported.
Customization
Backup software should allow you to customize your backups based on your requirements.
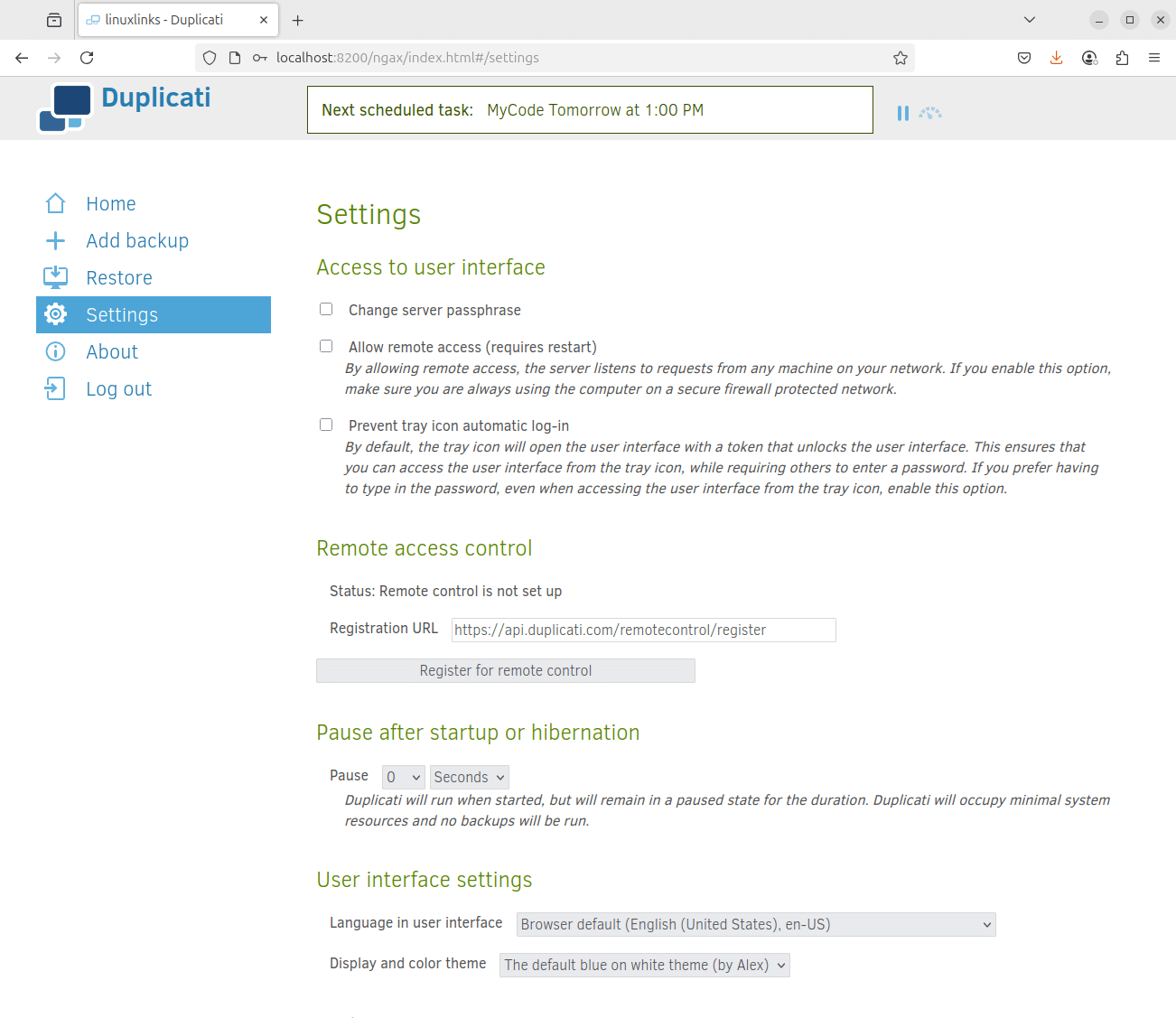
Duplicati offers a good range of customization options which are accessible from the Settings menu. We can set up remote access control, change settings for the user interface, as well as tons of advanced settings which let you configure http requests and core options.
Cloud support
Local backups won’t protect you from burglary or natural disasters.
Cloud support is one of the real strengths of Duplicati. Here’s an image showing the available options.

Documentation
Good backup software will provide clear documentation that explains how to use the software.
Duplicati’s documentation is very good although not all parts are completed. It’s easy to read, well organized and includes both a getting started guide and detailed descriptions of the software’s functionality.
Pages in this article:
Page 1 – Introduction and Installation
Page 2 – In Operation
Page 3 – Summary
