Last Updated on May 28, 2022
This is the ninth in our series of articles highlighting essential system tools. These are small utilities, useful for system administrators as well as regular users of Linux based systems. The series examines both graphical and text based open source utilities. For this article, we’ll look at Nmap (“Network Mapper”). For details of all tools in this series, please check the table in the summary section.
Nmap is widely regarded as the de facto standard tool for network exploration and security auditing. Network administrators use Nmap to identify devices running on their systems, discover available hosts and the services they offer, finding open ports and detecting security risks. While Nmap is often used for such security audits, many systems and network administrators find the tool helps with routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Nmap uses raw IP packets to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
The software was designed to rapidly scan large networks with thousands of devices and masses of subnets, although it monitors single hosts just as well.
Users who prefer a graphical interface can use the included Zenmap front-end.
Installation
Most popular Linux distributions provide convenient packages to install the software. There are also binaries available for Mac OS X and Windows. The developer has also created installation guides for FreeBSD, OpenBSD, NetBSD, Sun Solaris, Amiga, HP-UX and other operating systems.
The full source code is available to download, compile, and install.
In operation
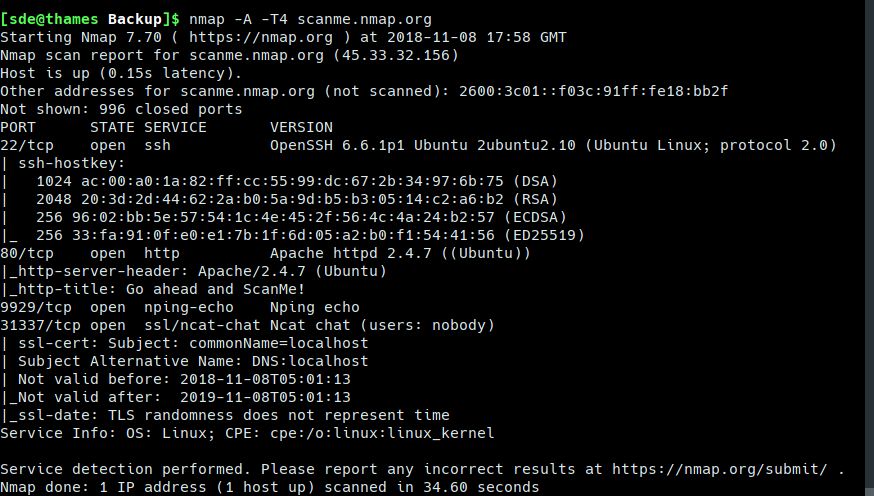
The above image shows a simple probe carried out by Nmap.
Nmap’s features include:
- Uses transport layer protocols including TCP (Transmission Control Protocol), UDP (User Datagram Protocol), and SCTP (Stream Control Transmission Protocol), as well as supporting protocols like ICMP (Internet Control Message Protocol), used to send error messages.
- Host discovery – Identifying hosts on a network. For example, listing the hosts that respond to TCP and/or ICMP requests or have a particular port open.
- Port scanning – Enumerating the open ports on target hosts.
- Version detection – Interrogating network services on remote devices to determine application name and version number.[7]
- OS detection – Determining the operating system and hardware characteristics of network devices.
- Scriptable interaction with the target – using Nmap Scripting Engine (NSE) and Lua programming language. Write, save and share scripts that automate different sorts of scans.
- Scans don’t have to generate significant traffic, and don’t need to be very intrusive with a range of intensities.
- Cross-platform support – runs under Linux, macOS, Windows, and other operating systems.
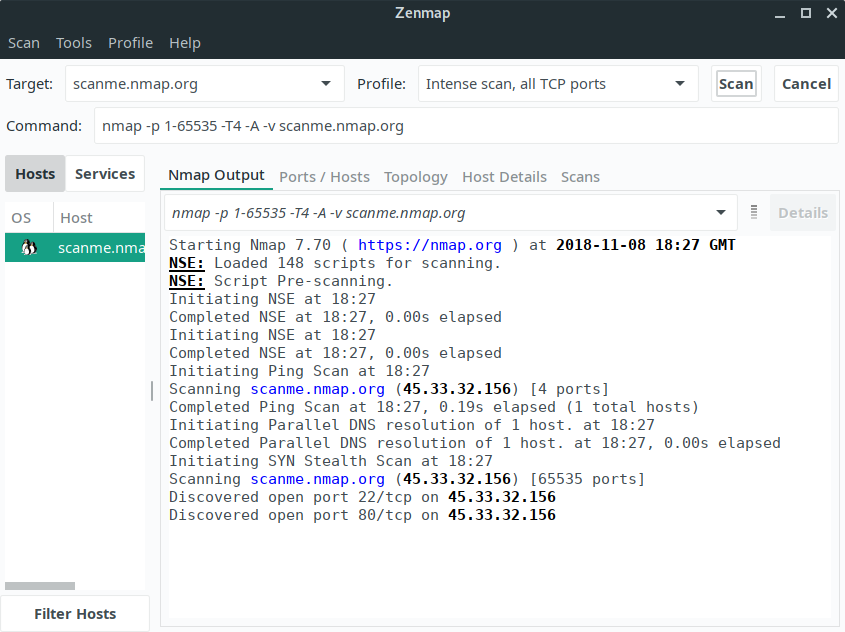
Here’s Zenmap in action.
Summary
Nmap is useful for beginners lacking detailed system or network knowledge, as well as professionals who can perform complex probes. It’s one of the most popular tools in its field.
Website: nmap.org
Support: Documentation, GitHub code repository
Developer: Gordon Lyon
License: Custom license, which is based on (but not compatible with) GPLv2
Nmap is written in C, C++ and Lua. Learn C with our recommended free books and free tutorials. Learn C++ with our recommended free books and free tutorials. Learn Lua with our recommended free books and free tutorials.
All the essential tools in this series:
| Essential System Tools | |
|---|---|
| Alacritty | Innovative, hardware-accelerated terminal emulator |
| BleachBit | System cleaning software. Quick and easy way to service your computer |
| bottom | Process/system monitor for the terminal |
| btop++ | Monitor usage and stats for CPU, memory, disks, network and processes |
| catfish | Versatile file searching software |
| Clonezilla | Partition and disk cloning software |
| CPU-X | System profiler with both a GUI and text-based |
| Czkawka | Find duplicate files, big files, empty files, similar images, and much more |
| ddrescue | Data recovery tool, retrieving data from failing drives as safely as possible |
| dust | More intuitive version of du written in Rust |
| f3 | Detect and fix counterfeit flash storage |
| Fail2ban | Ban hosts that cause multiple authentication errors |
| fdupes | Find or delete duplicate files |
| Firejail | Restrict the running environment of untrusted applications |
| Glances | Cross-platform system monitoring tool written in Python |
| GParted | Resize, copy, and move partitions without data |
| GreenWithEnvy | NVIDIA graphics card utility |
| gtop | System monitoring dashboard |
| gWakeOnLAN | Turn machines on through Wake On LAN |
| hyperfine | Command-line benchmarking tool |
| HyFetch | System information tool written in Python |
| inxi | Command-line system information tool that's a time-saver for everyone |
| journalctl | Query and display messages from the journal |
| kmon | Manage Linux kernel modules with this text-based tool |
| Krusader | Advanced, twin-panel (commander-style) file manager |
| Nmap | Network security tool that builds a "map" of the network |
| nmon | Systems administrator, tuner, and benchmark tool |
| nnn | Portable terminal file manager that's amazingly frugal |
| pet | Simple command-line snippet manager |
| Pingnoo | Graphical representation for traceroute and ping output |
| ps_mem | Accurate reporting of software's memory consumption |
| SMC | Multi-featured system monitor written in Python |
| Timeshift | Reliable system restore tool |
| QDirStat | Qt-based directory statistics |
| QJournalctl | Graphical User Interface for systemd’s journalctl |
| TLP | Must-have tool for anyone running Linux on a notebook |
| Unison | Console and graphical file synchronization software |
| VeraCrypt | Strong disk encryption software |
| Ventoy | Create bootable USB drive for ISO, WIM, IMG, VHD(x), EFI files |
| WTF | Personal information dashboard for your terminal |
