Last Updated on May 28, 2022
In Operation
The image below shows three mounted VeraCrypt volumes. As you can see, it mirrors the classic TrueCrypt interface.
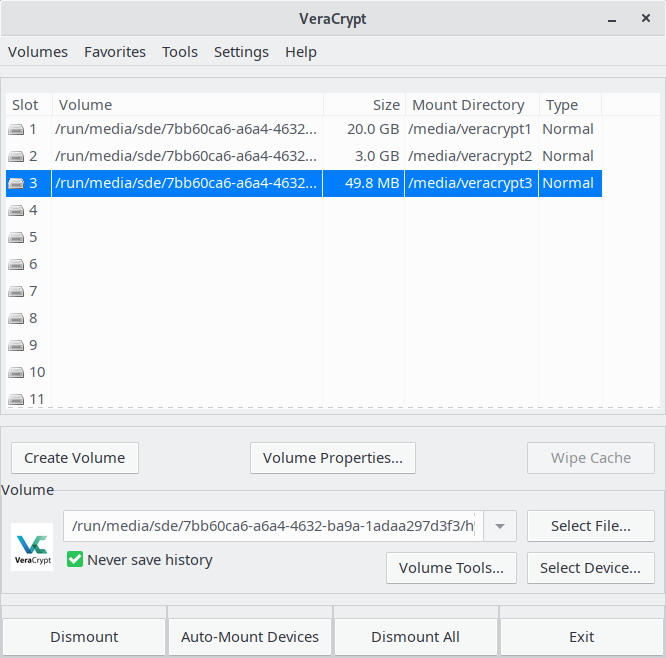
The software lets you mount and dismount volumes. You can add selected (or all) volumes as favorites, and there’s the option to organize them.
We always prefer software that help beginners. VeraCrypt ticks this box with a helpful volume creation wizard. With the wizard users can create an encrypted file container (recommended for inexperienced users), or create a volume within a partition/drive. Here’s an image of the wizard in action.
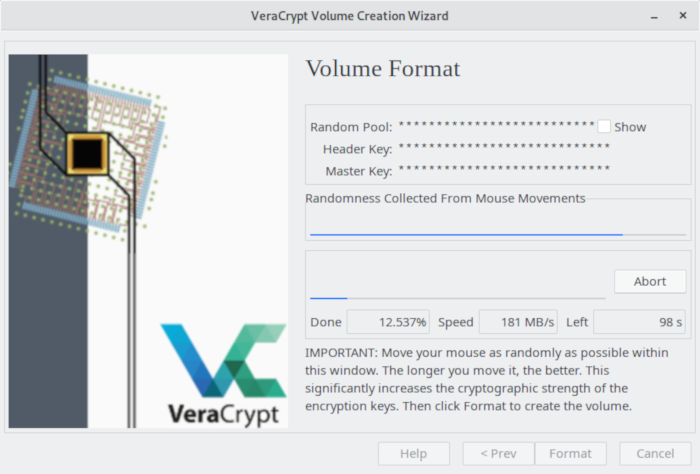
Volumes are divided into system volumes and non-system volumes. VeraCrypt supports both and can be used to keep all files as they are on a volume when you run the encrypt command.
With the encrypted file container, you can either create a normal VeraCrypt volume, or a hidden VeraCrypt volume. VeraCrypt supports plausible deniability by allowing a single “hidden volume” to be created within another volume.
VeraCrypt supports the following algorithms: AES, Serpent, Twofish, Kuznyechik, and Camellia. There’s also combinations of cascaded algorithms available with two or three different ciphers in a cascade. In a cascade, each block is first encrypted with an algorithm, and then encrypted with a different algorithm
The software supports RIPEMD-160, SHA-256, SHA-512, Whirlpool, and Streebog hash algorithms. VeraCrypt uses the XTS mode of operation.
VeraCrypt includes a tool to benchmark all supported encryption algorithms. That’s helpful as it tells you which algorithms offer the best performance.
Next page: Page 3 – Other Features
Pages in this article:
Page 1 – Introduction / Installation
Page 2 – In Operation
Page 3 – Other Features
Page 4 – Summary

I just installed VeraCrypt today. Coming from the Windows world, I used it for sensitive information, and today after 6 months on Linux, needed the security it offers.
You can fiddle with individual file/folder encryption, but why? I use the file container method and can take my encrypted info anywhere and with VeraCrypt in portable mode, I have access to it.
Nice article.