Security is paramount. Security involves defence in depth. Approaching security one step at a time, with consistency and rigour, you can mitigate threats, and keep intruders at bay.
Intruders use a variety of different techniques in an attempt to compromise a system. For example, systems can be attacked by denial of service, cracking, intrusion, snooping (intercepting the data of another user), or viruses/worms/Trojan horses. To have a secure box, a system therefore needs a variety of defences.
Vulnerability analysis is an essential activity for enterprise security.
Any competent enterprise will have a backbone of security measures including, but not limited to, a firewall, vulnerability scanner, asset-mapping, as well as a dedicated team that performs regular pentesting, an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system.
Recognizing, categorizing and characterizing security holes (known as vulnerabilities) among the network infrastructure, computers, hardware system, and software, etc. is known as Vulnerability Analysis.
The chart captures our recommendations. Only free and open source software is featured here.
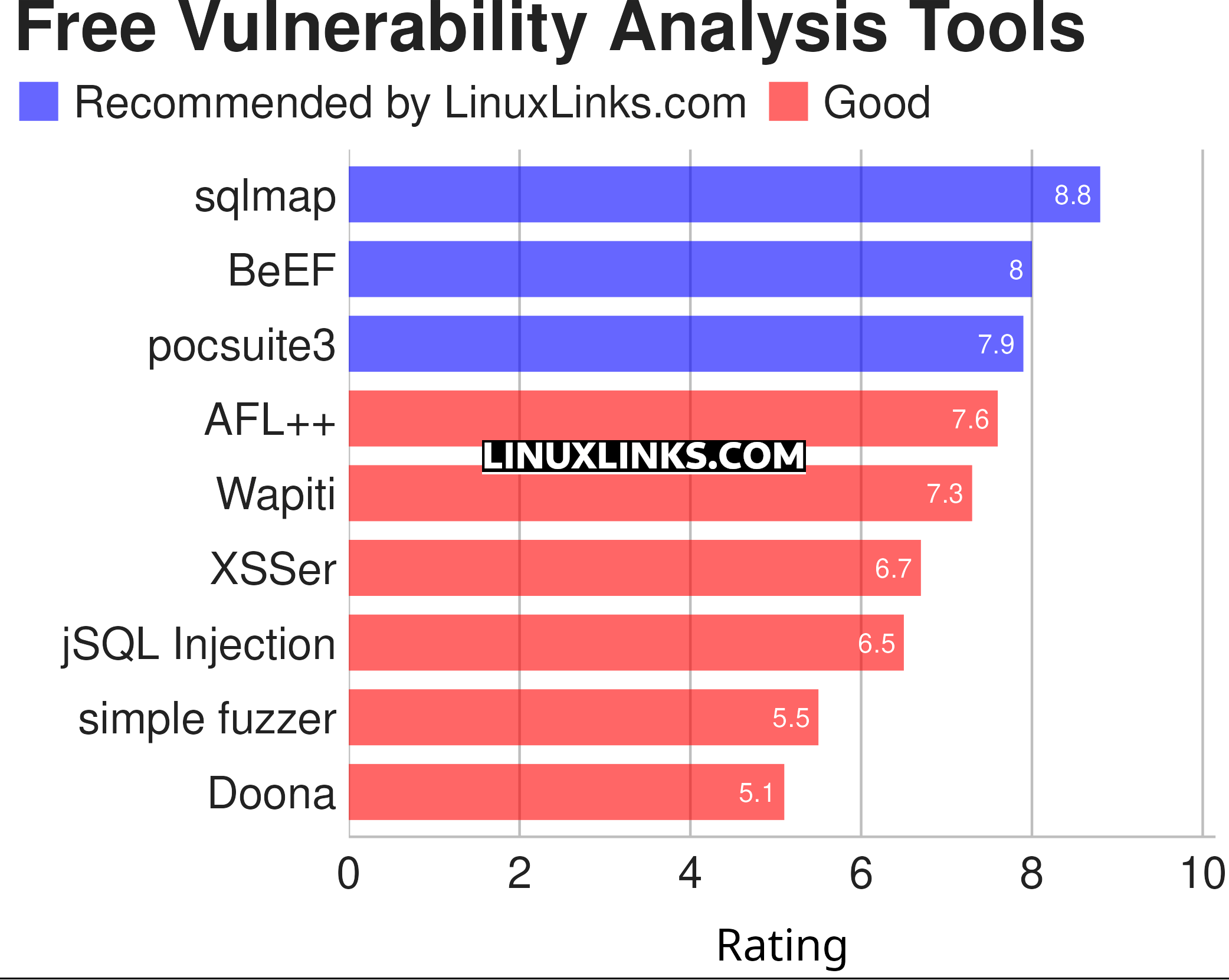
Let’s explore the 9 tools. For each application we have compiled its own portal page, a full description with an in-depth analysis of its features, together with links to relevant resources.
| Vulnerability Analysis Tools | |
|---|---|
| sqlmap | Penetration testing tool |
| BeEF | The Browser Exploitation Framework |
| pocsuite3 | Remote vulnerability testing framework |
| AFL++ | Security-oriented fuzzer |
| Wapiti | "Black-box" vulnerability scanner |
| XSSer | Detect, exploit and report XSS vulnerabilities |
| jSQL Injection | Automatic SQL database injection |
| simple fuzzer | A fuzzer with two network modes of operation |
| Doona | Fork of the Bruteforce Exploit Detector Tool |
 Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Read our complete collection of recommended free and open source software. Our curated compilation covers all categories of software. Spotted a useful open source Linux program not covered on our site? Please let us know by completing this form. The software collection forms part of our series of informative articles for Linux enthusiasts. There are hundreds of in-depth reviews, open source alternatives to proprietary software from large corporations like Google, Microsoft, Apple, Adobe, IBM, Cisco, Oracle, and Autodesk. There are also fun things to try, hardware, free programming books and tutorials, and much more. |